Huawei基于双机热备主备模式的IPsec
拓扑
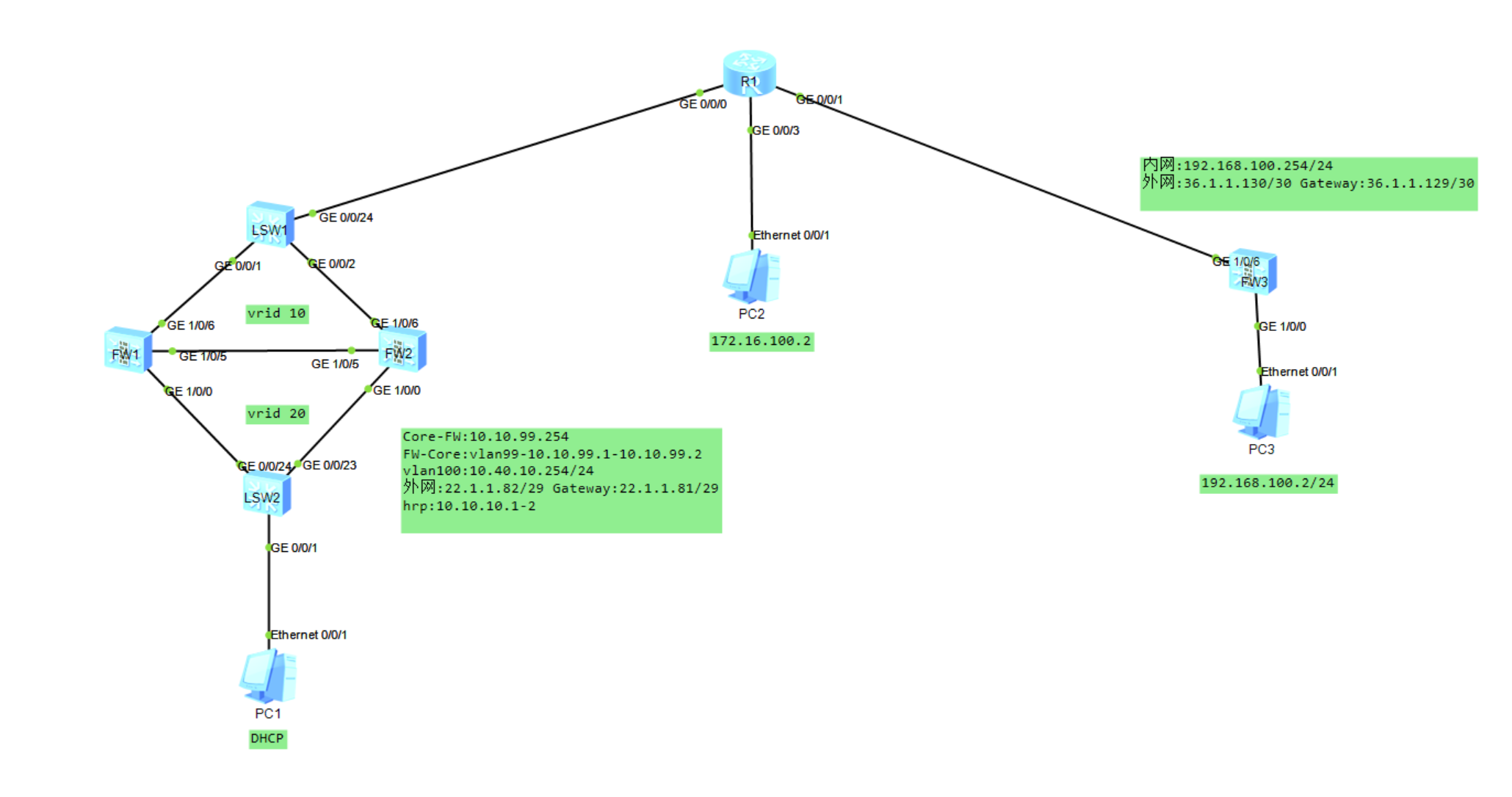
规划
总部
Core-FW:10.10.99.254
FW-Core:vlan99-10.10.99.1-10.10.99.2
vlan100:10.40.10.254/24
外网:22.1.1.82/29 Gateway:22.1.1.81/29
hrp:10.10.10.1-2
分部
内网:192.168.100.254/24
外网:36.1.1.130/30 Gateway:36.1.1.129/30
FW1配置
!Software Version V500R005C10SPC300
!Last configuration was saved at 2025-06-19 02:58:23 UTC
#
sysname USG6000V1
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/5 remote 10.10.10.2
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/6
#
update schedule location-sdb weekly Sun 06:45
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 23:51
update schedule av-sdb daily 23:51
update schedule sa-sdb daily 23:51
update schedule cnc daily 23:51
update schedule file-reputation daily 23:51
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
acl number 3000
rule 5 permit ip source 10.40.0.0 0.0.255.255 destination 192.168.100.0 0.0.0.255
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer b
pre-shared-key %^%#/.!Q-^ITD'zcqFVSi*nQ~U|<$OCG<T,.%6(~b*rB%^%#
ike-proposal 10
dpd type on-demand
remote-address 36.1.1.130
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer b
proposal tran1
tunnel local 22.1.1.82
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%IeaX%RCdu3{*xE,9#xcKfcBLXN\AG{WD!>hdbD@RVK\%cBOf@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%;c4;H(10{QLdG0#Ps!4=B#'>hC$=2$*yC8k<z*,rJ%z'#'AB@%@%
level 15
manager-user admin
password cipher @%@%+)s@M&B7S)N]Cx8aI`D<1yC|ED!f3~@(c%'M$A#W4AF+yC"1@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.10.99.1 255.255.255.0
vrrp vrid 20 virtual-ip 10.10.99.253 active
vrrp virtual-mac enable
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
ip address 10.10.10.1 255.255.255.0
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 10.10.100.1 255.255.255.0
vrrp vrid 10 virtual-ip 22.1.1.82 255.255.255.248 active
vrrp virtual-mac enable
service-manage ping permit
ipsec policy map1
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/5
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 22.1.1.81
ip route-static 10.40.0.0 255.255.0.0 10.10.99.254
ip route-static 192.168.100.0 255.255.255.0 22.1.1.81
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
nat address-group 1 0
mode pat
route enable
section 0 22.1.1.82 22.1.1.86
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name Internet
source-zone trust
destination-zone untrust
action permit
rule name ipsec1
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name ipsec2
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.40.0.0 mask 255.255.0.0
source-address 192.168.100.0 mask 255.255.255.0
destination-address 10.40.0.0 mask 255.255.0.0
destination-address 192.168.100.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name ipsec
source-zone trust
destination-zone untrust
source-address 10.40.0.0 mask 255.255.0.0
destination-address 192.168.100.0 mask 255.255.255.0
action no-nat
rule name Internet
source-zone trust
destination-zone untrust
action source-nat address-group 1
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return FW2配置
!Software Version V500R005C10SPC300
!Last configuration was saved at 2025-06-19 02:58:35 UTC
#
sysname USG6000V1
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/5 remote 10.10.10.1
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/6
#
update schedule location-sdb weekly Sun 00:44
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 02:04
update schedule av-sdb daily 02:04
update schedule sa-sdb daily 02:04
update schedule cnc daily 02:04
update schedule file-reputation daily 02:04
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
acl number 3000
rule 5 permit ip source 10.40.0.0 0.0.255.255 destination 192.168.100.0 0.0.0.255
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer b
pre-shared-key %^%#/.!Q-^ITD'zcqFVSi*nQ~U|<$OCG<T,.%6(~b*rB%^%#
ike-proposal 10
dpd type on-demand
remote-address 36.1.1.130
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer b
proposal tran1
tunnel local 22.1.1.82
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%0)glT4ecAO,[1=ZJ!_U)397vU~G;Vrbe*R_(IGBk<pm/97y3@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%&%ab+f6(k-MQS(>*PBk$GCBIO\xKF_rA#PYO_`AQBVP*CBLG@%@%
level 15
manager-user admin
password cipher @%@%$d687eqp\~$<[uR=d[.7-S`]#,`.8'C^]G<c@u=llWN4S``-@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.10.99.2 255.255.255.0
vrrp vrid 20 virtual-ip 10.10.99.253 standby
vrrp virtual-mac enable
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
ip address 10.10.10.2 255.255.255.0
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 10.10.100.2 255.255.255.0
vrrp vrid 10 virtual-ip 22.1.1.82 255.255.255.248 standby
vrrp virtual-mac enable
service-manage ping permit
ipsec policy map1
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/5
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 22.1.1.81
ip route-static 10.40.0.0 255.255.0.0 10.10.99.254
ip route-static 192.168.100.0 255.255.255.0 22.1.1.81
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
nat address-group 1 0
mode pat
route enable
section 0 22.1.1.82 22.1.1.86
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name Internet
source-zone trust
destination-zone untrust
action permit
rule name ipsec1
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name ipsec2
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.40.0.0 mask 255.255.0.0
source-address 192.168.100.0 mask 255.255.255.0
destination-address 10.40.0.0 mask 255.255.0.0
destination-address 192.168.100.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name ipsec
source-zone trust
destination-zone untrust
source-address 10.40.0.0 mask 255.255.0.0
destination-address 192.168.100.0 mask 255.255.255.0
action no-nat
rule name Internet
source-zone trust
destination-zone untrust
action source-nat address-group 1
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return Core配置
#
sysname Core
#
vlan batch 99 to 100
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
dhcp enable
#
diffserv domain default
#
drop-profile default
#
ip pool vlan100
gateway-list 10.40.10.254
network 10.40.10.0 mask 255.255.255.0
dns-list 223.5.5.5
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif99
ip address 10.10.99.254 255.255.255.0
#
interface Vlanif100
ip address 10.40.10.254 255.255.255.0
dhcp select global
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/2
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
port link-type access
port default vlan 99
#
interface GigabitEthernet0/0/24
port link-type access
port default vlan 99
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 10.10.99.253
#
user-interface con 0
user-interface vty 0 4
#
returnFW3配置
!Software Version V500R005C10SPC300
!Last configuration was saved at 2025-06-19 03:09:41 UTC
#
sysname FW-CZ
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 06:49
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 00:32
update schedule av-sdb daily 00:32
update schedule sa-sdb daily 00:32
update schedule cnc daily 00:32
update schedule file-reputation daily 00:32
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
acl number 3000
rule 5 permit ip source 192.168.100.0 0.0.0.255 destination 10.40.0.0 0.0.255.255
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer b
pre-shared-key %^%#$;q6E2@Js63'25HlnJFZGQ/CH+-g:Dy)9gKS{9'F%^%#
ike-proposal 10
dpd type on-demand
remote-address 22.1.1.82
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer b
proposal tran1
tunnel local 36.1.1.130
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%t:Sm'klcU~@C>U4X/>fMpY;a85QkS"+qp@69^b/e~m}$Y;dp@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%Y43D/.]i2YFtTL*KT=h~kgi=Tx+UB!SA[/n40z)x%n=+gi@k@%@%
level 15
manager-user admin
password cipher @%@%[]_QEr$o*4+\n~6uW:-L~aAt)h(!6|oI)<+b;o<PaV::aAw~@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.100.254 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 36.1.1.130 255.255.255.252
service-manage ping permit
ipsec policy map1
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/6
#
firewall zone dmz
set priority 50
#
ip route-static 0.0.0.0 0.0.0.0 36.1.1.129
ip route-static 10.40.0.0 255.255.0.0 36.1.1.129
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name Internet
source-zone trust
destination-zone untrust
action permit
rule name ipsec1
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name ipsec2
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.40.0.0 mask 255.255.0.0
source-address 192.168.100.0 mask 255.255.255.0
destination-address 10.40.0.0 mask 255.255.0.0
destination-address 192.168.100.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name ipsec
source-zone trust
destination-zone untrust
source-address 192.168.100.0 mask 255.255.255.0
destination-address 10.40.0.0 mask 255.255.0.0
action no-nat
rule name Internet
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return 